Protect Website
Support Wissensdatenbank
-
Administration
- 30 Days Money Back
- Cancel a contract
- Change address data
- Change contact person (company)
- Change password
- Display bills
- Fewer Invoices
- Invoice by mail
- Manage Contacts
- Partner administration
- Password Forgotten
- Payment methods
- Payment slip
- Product Transfer
- Recruiting friends
- Reminder
- Server Data Centre
- Setting up two-factor authentication
- Top up credit
- Webmail Link
-
Cloud Storage
-
DNS Service
-
Domain
- .ZUERICH DOMAINS Register
- Activate Whois Privacy
- Cancel domain
- Change contacts
- Change DNS entries
- Change DNS Server
- Check DNSSEC
- Configure domain for mail traffic
- Connect website to Squarespace
- Connect website with Wix
- Connect your website to Jimdo
- Difference in domain redirect
- DNSSEC
- DNSSEC Deactivate
- Enable domain forwarding
- Extend domain
- Google Optimization
- Google search optimization
- Google SiteVerification
- Link domain
- Questions about the domain
- Search engine registrationa
- Set up your own SPF server
- Transfer domain
-
E-Mail
- Are our e-mails encrypted?
- Automatic e-mail reply
- Change password
- Customize e-mail addresses in the Microsoft Portal
- external name servers
- Important SPF entries
- JUNK Mail in Outlook
- Mail Log
- Newsletter Server important questions
- Office365 Logout and Setup
- Report SPAM Mails
- Send e-mails
- Send email as attachment
- Set up email alias
- Setting up an email account in Thunderbird
- SPF entry
- Webmail Link
- Webmail Login does not work
-
Einrichtung
-
Server
-
-
- Add module PGSQL in PHP
- Change IP at Confixx
- Confixx 3.1 End User Manual
- Confixx 3.1 Special Edition Manual for Administrators
- Confixx Server DBD::mysql or other PERL module displays error message
- Release Confixx database
- Setting up Apache server compression in Debian
- Setting up Apache server compression in SuSE
- Swap Confixx license
-
- Add PHP version to chrooted
- Apache2 does not start
- Automatic detection with Plesk Server (Linux)
- Create customer in reseller hosting
- Install Node.JS version
- LINUX: Apache Crash at log rotation at UBUNTU
- LINUX: MySQL Upgrade von 5.5 auf 5.6 mit Ubuntu
- Linux: Restart Network Interface
- Linux: Too many open files in Ubuntu
- List storage space from Reseller
- Plesk can't start PHP-fpm
- Plesk Linux: Enable NGINX and HTTP/2
- Plesk Log Files
- Repairing databases
- Special character problems
- Upgrade MSSQL Server
- Use PHP version
- Allow Support Team Access
- Backup setup
- Convert Ubuntu MBR to GPT
- Empty directory quickly
- Empty Mailq
- Enlarge partition at Ubuntu 16.04
- How do I log in via SSH?
- Monitoring of RAID controllers
- MySQL with Docker
- Optimize your server
- Proxmox installation problem: Fix Black Screen
- Questions about the root servers
- Reinstallation
- Remove Ubuntu old kernels
- Repair Mysql / MariaDB databases
- repair quota
- Resetting Windows password
- restore very old website
- Server does not boot
- Set up Mysql replication server
- Setting up Jitl
- SNF filter does not start
- Start NGINX manually
- Windows Server 2019 Change language
- WordPress installieren
-
-
-
ShopDesigner
-
- 1.00 The most important questions about ShopDesigner
- 1.01 Set up your online shop
- 1.02 Add products to your online shop
- 1.05 Product categories and keywords
- 1.06 Inventory and Inventory Tracking
- 1.07 Shipping options
- 1.08 Tax rates
- 1.09 Importing products from a CSV file
- 1.10 product variants
- 1.11 AGB for your OnlineShop
- 1.13 Set currency
- 1.16 OnlineShop Analysis
- Add Google Calendar
- Booking and calendar tool for SiteDesigner
- SiteDesigner Backup
-
-
SiteDesigner
-
- 01 Adding and moving content
- 02 Colors and fonts
- 03 Website designs
- 04 Use a stock image
- 05 change an image
- 06 Add page
- 07 Set up a store
- 09 Site analytics
- 1.01 SiteDesigner Quickstart
- 1.02 Add basic page information
- 1.03 Change the appearance of your page
- 1.04 Pictures, Galleries and Presentations
- 1.05 Text and headings
- 1.09 Hide incomplete pages
- 1.10 Forms, cards and other content
- 1.11 Setting Language, Currency and Units
- 1.14 Re-sort and rearrange pages
- 1.15 SiteDesigner Mobile and mobile phone quick start
- 1.16 SiteDesigner Tablet Quickstart
- 1.17 How does the Template Editor work?
- 1.20 Undo changes
- 1.22 Setting up a user-defined contact form
- 10 Setup a blog
- 12 Multiple language sites
- 15 Contact forms
- Add Google Analytics
- Add Google Calendar
- add more pages to SiteDesigner
- Add number of pages to my page
- Add type of content to my website
- Advantage of SiteDesigner
- Create a link to any page
- Definition SiteDesigner
- Edit Site Template CSS
- Edit SiteDesigner with HTML code
- Embed external website
- Export page from SiteDesigner and send it to another server via FTP
- good page ranking?
- pay by phone with credit card
- Request Backup
- Request emergency service
- SiteDesigner Move Package
- Take website offline
- Webhosting to the SiteDesigner?
-
SMS Gateway
-
SSL Certificates
- Activate SSL certificate
- Activate SSL certificate for forwarding
- Browser is not supported
- Certification Requirement (CSR)
- Conditions to be fulfilled
- Creating a Certification Requirement (CSR) for Apache
- Definition SSL CERTIFICATE
- Difference Domain and Identity Certification
- Intermediate certificate
- Let's Encrypt does not work
- Requirements for issuing an SSL Certificate
- SiteSeal
- SSL in Java Keystore
- the right certificate
- Wildcard certificate
-
Technical
-
- add a new node to the cluster
- Add LVM-Thin
- Cache Settings
- CloudInit set up
- Import Windows
- Important Proxmox commands
- LVM Rename
- Migration shows no progress
- Nested Virtualisation
- Proxmox shutdown
- Proxmox with Highpoint does not boot
- Proxmox with question Mark
- Remove Proxmox VM Disk
- Repair Proxmox Cluster
- Run Proxmox with NVME RAID
- Run Proxmox with NVME RAID
- VM hangs: Booting from Harddisk
-
-
Webhosting
-
-
- Bugfix: Wordpress does not work anymore
- Copy WordPress
- Customizing the domain of a Wordpress website
- Increase PHP timeout
- load-scripts.php 500 Internal server error
- Permalinks in Wordpress (Windows)
- Rename URL
- Switch off Wordpress maintenance mode
- Transfer Wordpress Website
- WordPress - Login button is not displayed
- Wordpress DSGVO Tools (GDPR) hacked
- Wordpress DSGVO Tools (GDPR) hacked
- Wordpress login doesn't work, password reset doesn't work either
- xml-rpc.php Forbidden
- Activate SSL certificate
- add another user
- Advantages of a website
- Blocking access for certain countries
- Browser Error Codes
- Disable Website Cache
- Enable Directory Listing
- external access to database server
- Log in to Plesk
- Moving Hosting Package
- NodeJS Setup
- PHP disabled functions
- Planning tasks
- Plesk Backup Manager
- Protect Website
- Request Backup
- restore very old website
- Ruby einrichten
- Transfer Website
-
Protect Website
You want to protect your website against Cross Site Scripting or Phishing? Then follow these instructions and check if your website works.
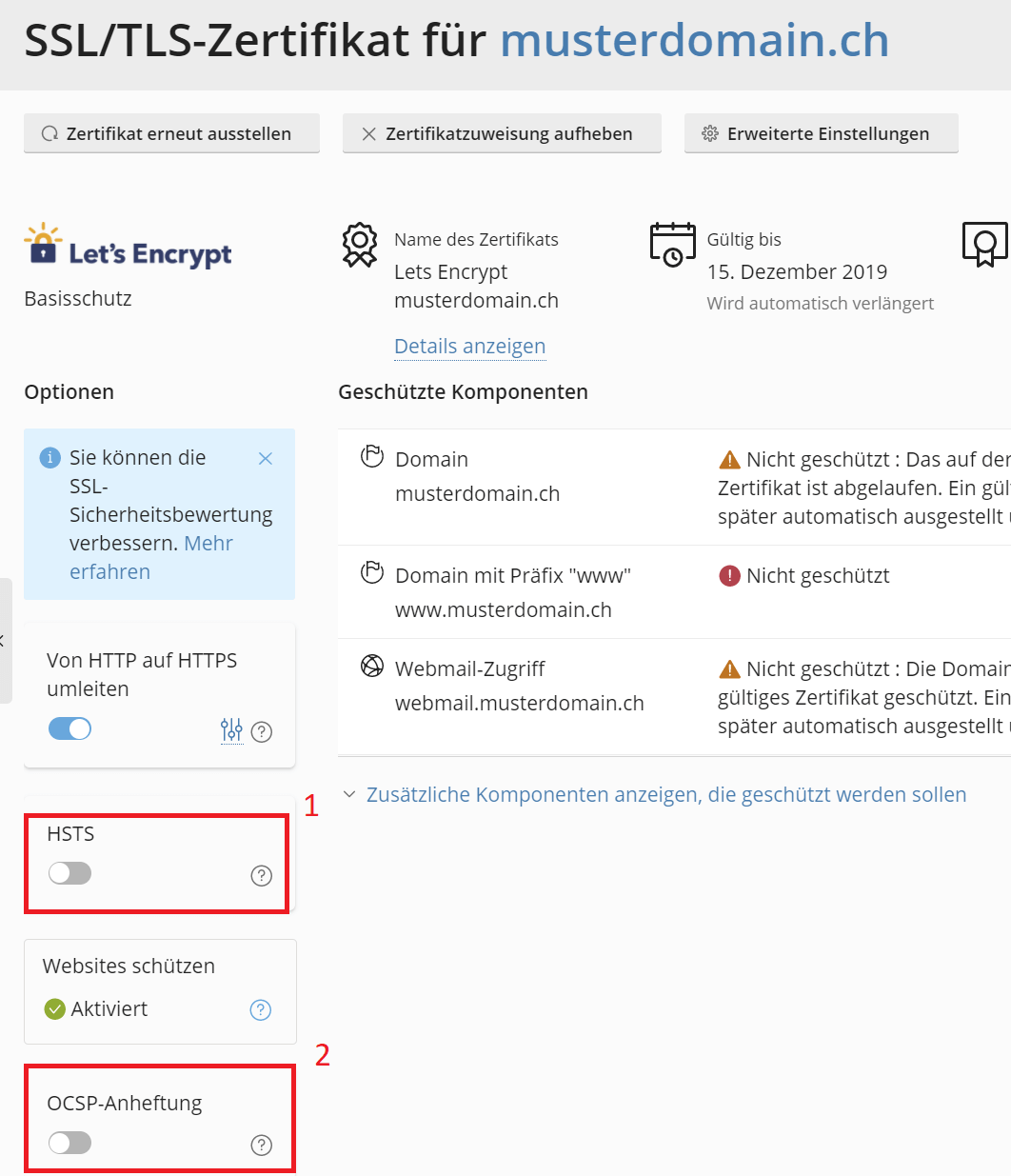
1. In the hosting administration you activate HSTS [1] and OCSP [2] in the SSL settings.
2. Now create a .htaccess in your main domain directory and add the following code:
#FireStorm Security Headers <IfModule mod_headers.c> Header set X-Content-Type-Options nosniff Header set X-Frame-Options "SAMEORIGIN" Header set Referrer-Policy "no-referrer" Header set Permissions-Policy "fullscreen=(), geolocation=()" Header set X-XSS-Protection "1; mode=block" </IfModule>
If you want to block everything external except musterdomain.ch and externedomain.tld:
#FireStorm Security Headers <IfModule mod_headers.c> Header set X-Content-Type-Options nosniff Header set X-Frame-Options "SAMEORIGIN" Header set Referrer-Policy "no-referrer" Header set Permissions-Policy "fullscreen=(), geolocation=()" Header set X-XSS-Protection "1; mode=block" Header set Content-Security-Policy "default-src 'self' *.musterdomain.ch *.externedomain.tld " </IfModule>
3. Now log into Plesk. Open the Domain => Hosting Settings => Apache & NGINX Settings and add the following value under Additional Apache statements for HTTP and HTTPS:
Header always edit Set-Cookie ^(.*)$ $1;HttpOnly;Secure
4. If you check your website, you should get the highest award at the following link: https://securityheaders.com/.
5. Now check your website if everything is still working properly.
Activate DANE
We recommend a static SSL certificate for DANE, which must be purchased on our website. The process must be repeated each time the certificate is changed!
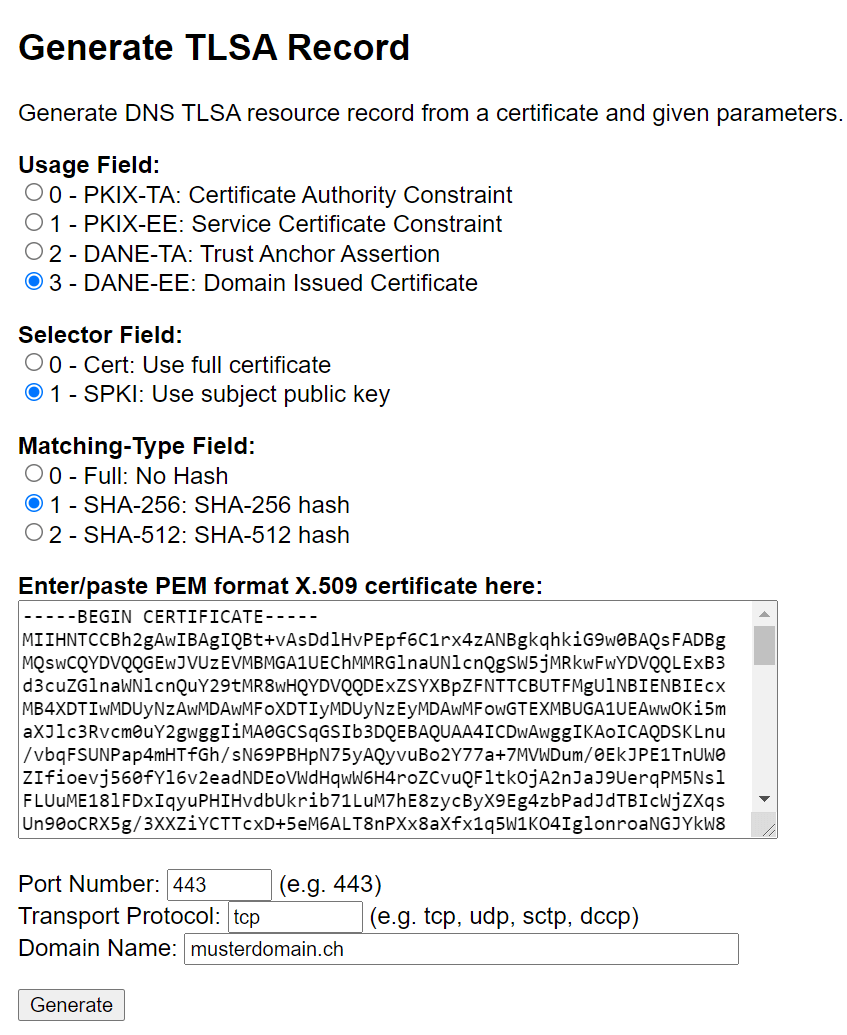
1. Open your website. Click on the key at the top of the address bar and then on certificate information. Click on “Details => Copy to file….”. Now save the file as Base-64 encoded x.509 (.cer).
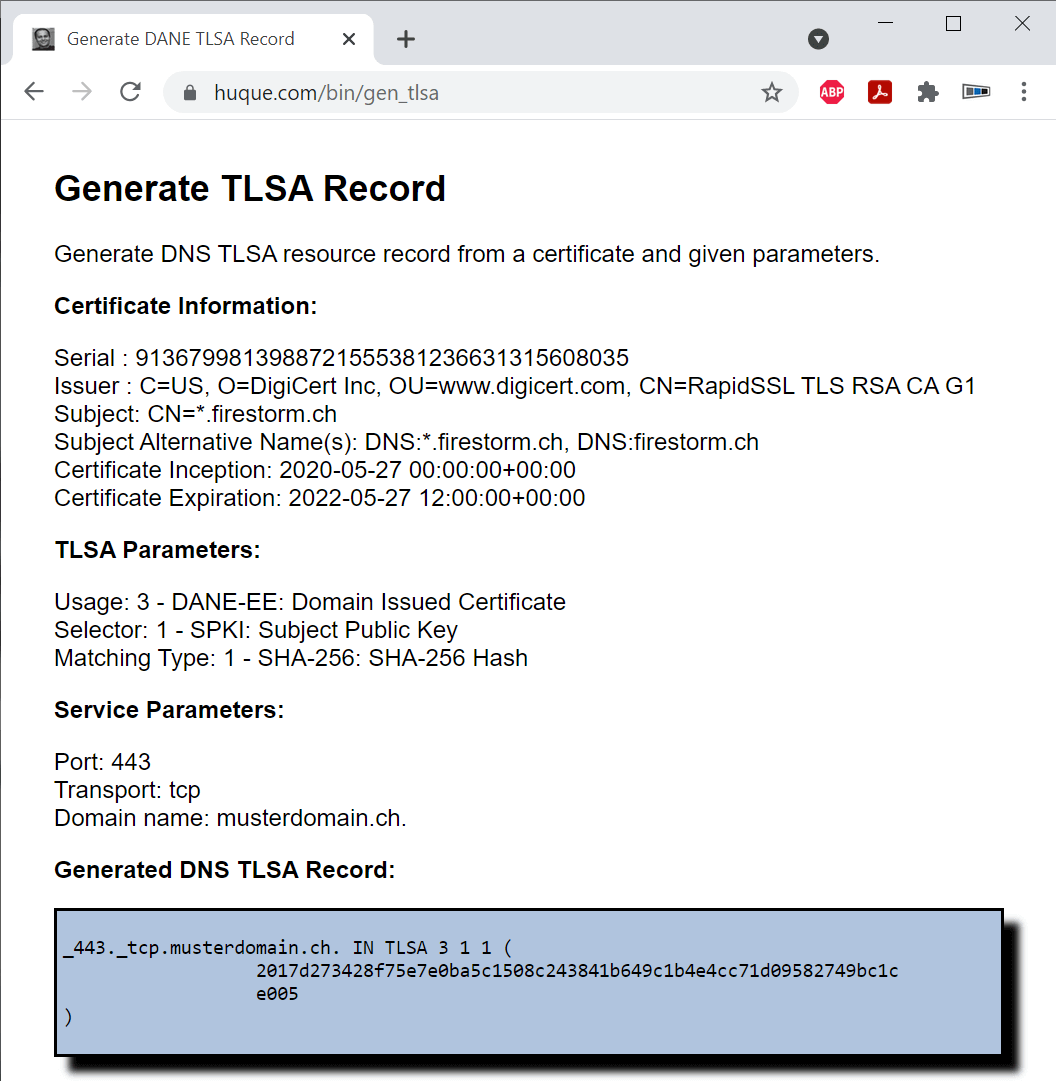
2. Now open the website https://www.huque.com/bin/gen_tlsa and fill in the form as follows:
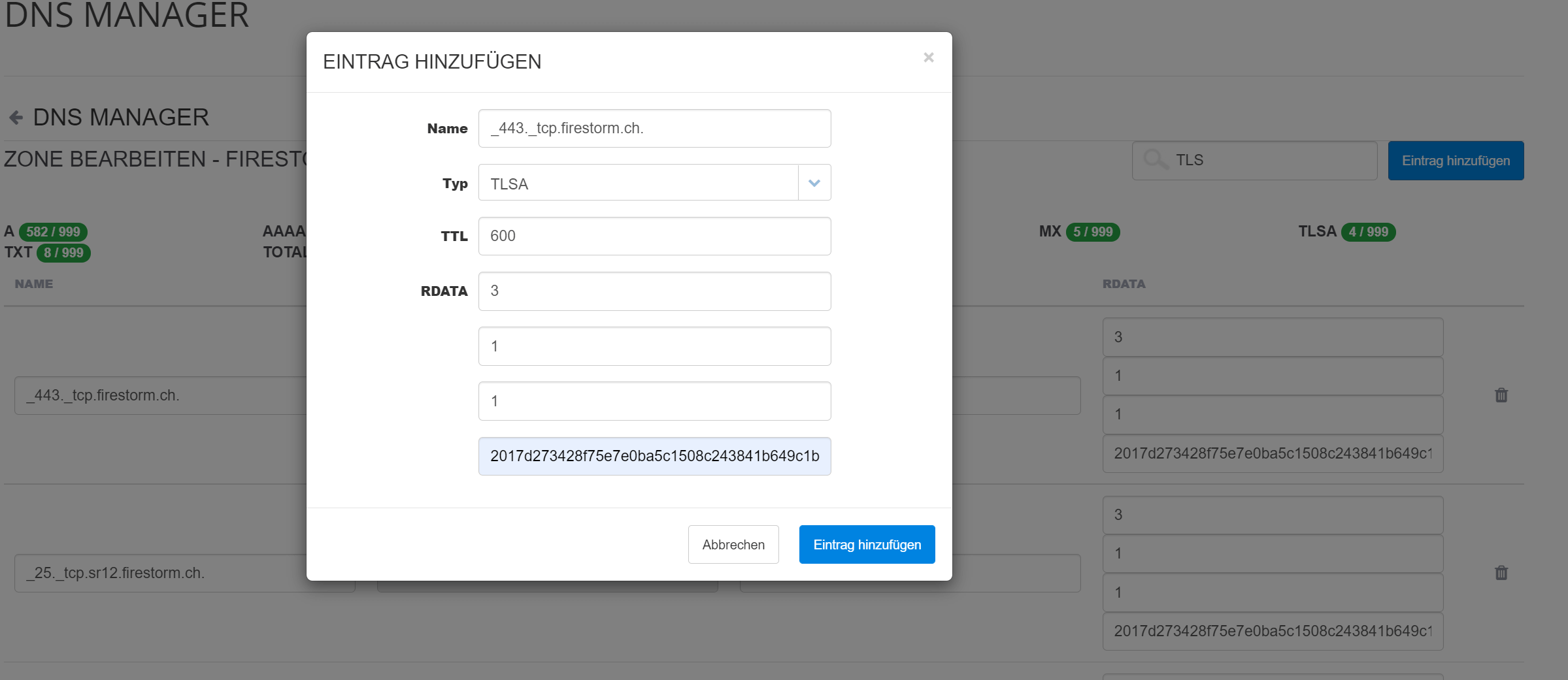
3. Now open the DNS administration of your domain and transfer the previously generated data as in the example. Create a new entry for this purpose:
Name: _433._tcp.firestorm.ch
Typ: TLSA
TTL: 600
RDATA: 3
RDATA: 3
RDATA: 1
RDATA: 2017d273428f5e7e0ba….
Add another entry for each system stored as MX server. For example, _25._tcp.mail.musterdomain.ch if your MX mail server is mail.musterdomain.ch. Please make sure that the mail server also responds to the same certificate.
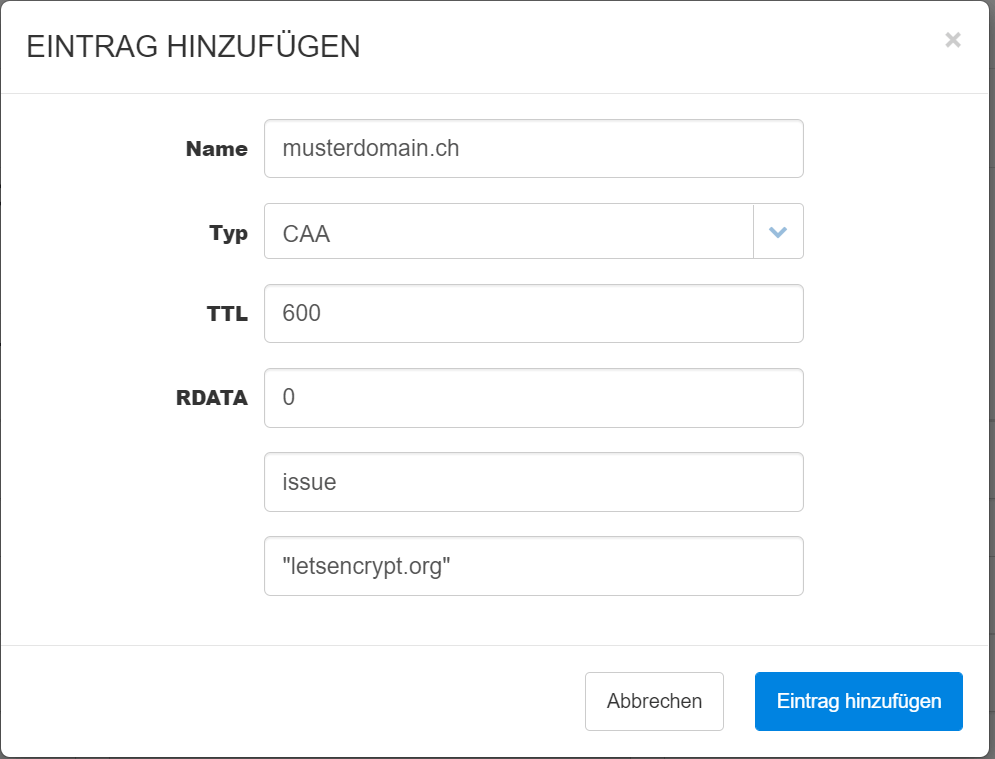
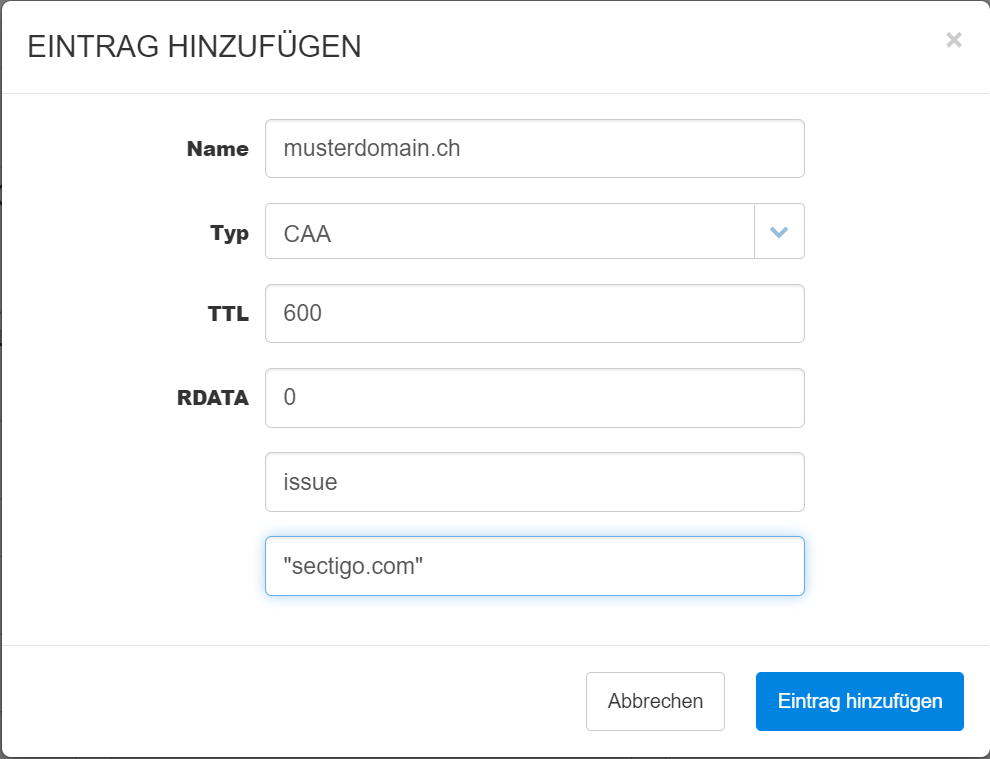
4. Create CAA, restrict the certificate issuers.
Only allow certificate issuers that you have explicitly allowed. To do this, open the DNS Manager and add the following rule:
Example to allow Let’s Encrypt:
Example to allow Sectigo:
Activate MTA-STS
1. Create the following file in the FileManager with the following content (Please match musterdomain.ch with your own domain):
https://mta-sts.musterdomain.ch/.well-known/mta-sts.txt
version: STSv1 mode: testing mx: mail.musterdomain.ch max_age: 86400
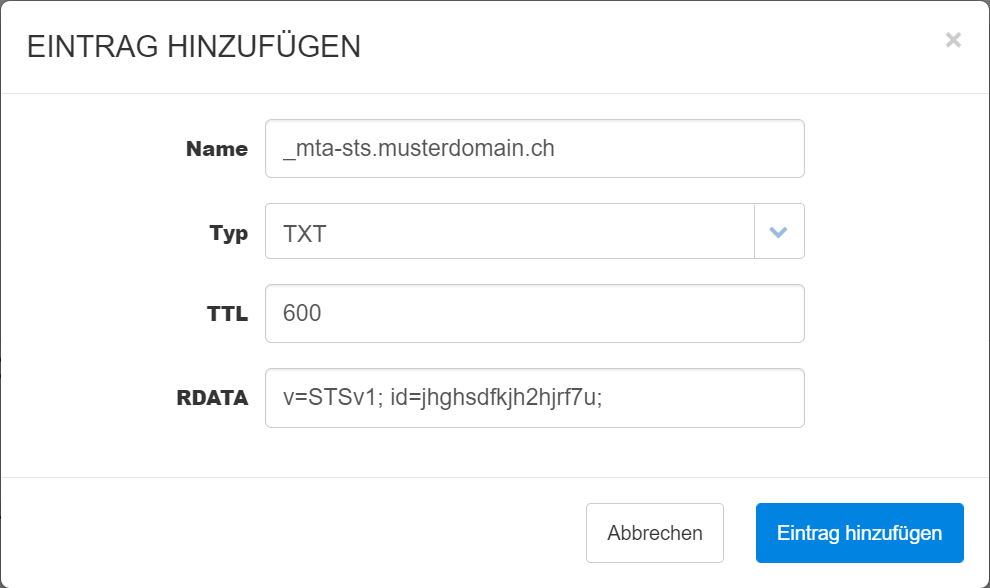
2. Now create a new DNS entry with the following value:
Name: _mta-sts.musterdomain.ch
Typ: TXT
TTL: 600
RDATA: v=STSv1; id=jhghsdfkjh2hjrf7u;
Replace jhghsdfkjh2hjrf7u with your own unique key. As soon as the certificate changes, you have to change the ID!
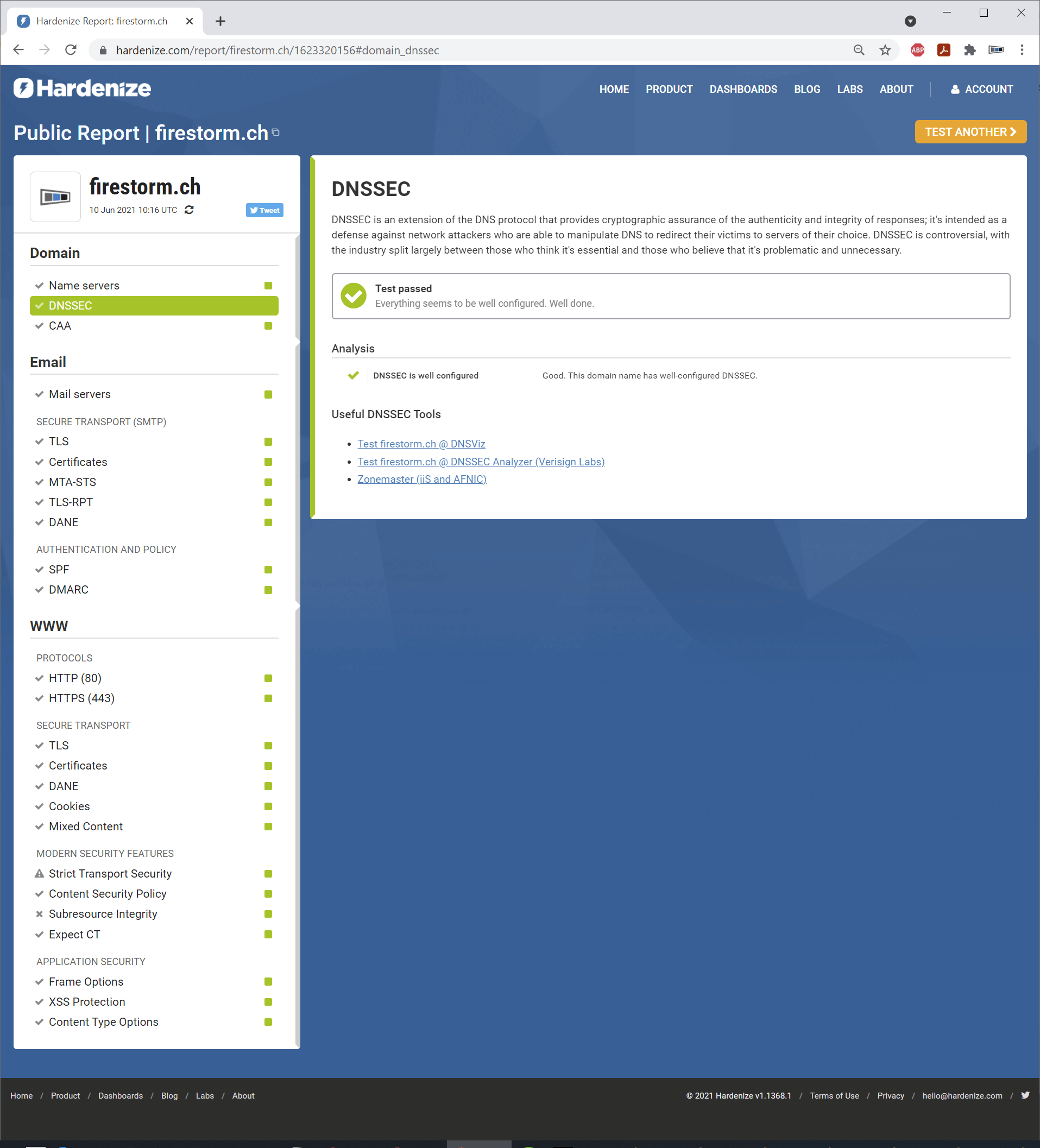
3. Now check your website at hardenize.com. The output may look like this, for example:
IMPORTANT:
If the SSL for *.musterdomain.ch is changed, the TLSA entries must be adjusted and it must be ensured that all registered MX mail servers have the new SSL certificate installed. Finally, a new ID must be set in the file https://mta-sts.musterdomain.ch/.well-known/mta-sts.txt.
0 out Of 5 Stars
| 5 Stars | 0% | |
| 4 Stars | 0% | |
| 3 Stars | 0% | |
| 2 Stars | 0% | |
| 1 Stars | 0% |